WNE Security News
Read more about “How to Create Secure Session Management: Best Practices for Web Applications” and the most important cybersecurity news to stay up to date with
How to Create Secure Session Management: Best Practices for Web Applications

WNE Security Publisher
10/10/2024

Learn about How to Create Secure Session Management: Best Practices for Web Applications and other new best practices and newly exploited vulnerabilities by subscribing to our newsletter.
Guide to Secure Session Management Practices
Secure session management is critical to ensuring that user sessions in web applications are protected from common cyberattacks like session hijacking, session fixation, and Cross-Site Request Forgery (CSRF). A session allows a web application to maintain a continuous interaction with a user across multiple requests. Poor session management can lead to unauthorized access and data breaches.
This guide explains secure session management practices, focusing on key areas such as generating unique session IDs, using HTTPS, setting secure cookies, and implementing session timeout policies.
Generating Unique Session IDs
Session IDs are unique identifiers used by the server to distinguish between different users’ sessions. A securely generated session ID is essential because if an attacker can guess or predict the session ID, they can hijack the session.
Best practices for session ID generation:
- Use cryptographically secure random generators for creating session IDs.
- Ensure that the session ID is long enough (typically 128 bits or more) to prevent brute-force attacks.
- Regenerate session IDs after login or privilege escalation to prevent session fixation attacks, where an attacker pre-assigns a session ID and tricks a user into using it.
Example: Secure Session ID Generation in PHP
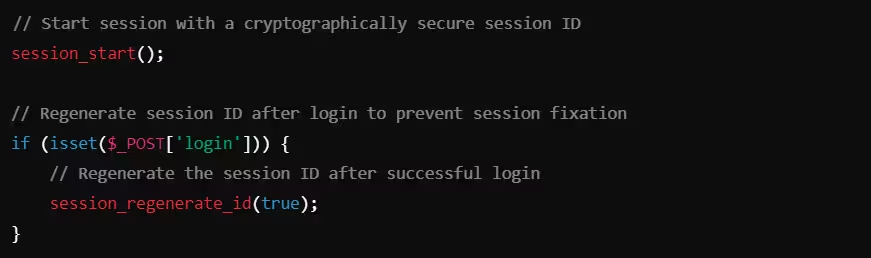
In this example, PHP’s session_regenerate_id(true) regenerates the session ID securely, ensuring that a new session ID is created after login, protecting against session fixation attacks.
Using HTTPS for Secure Session Transmission
Using HTTPS (SSL/TLS) is crucial for protecting session IDs during transmission. Without HTTPS, session IDs and other sensitive data are sent in plain text over the network, making them vulnerable to man-in-the-middle (MITM) attacks.
Best practices for using HTTPS:
- Ensure that all pages, not just login pages, are served over HTTPS to protect session data.
- Redirect any HTTP traffic to HTTPS, and enforce HTTPS by using the Strict-Transport-Security (HSTS) header, which tells browsers to only access the site over HTTPS.
Example: Enforcing HTTPS in Express.js (Node.js)
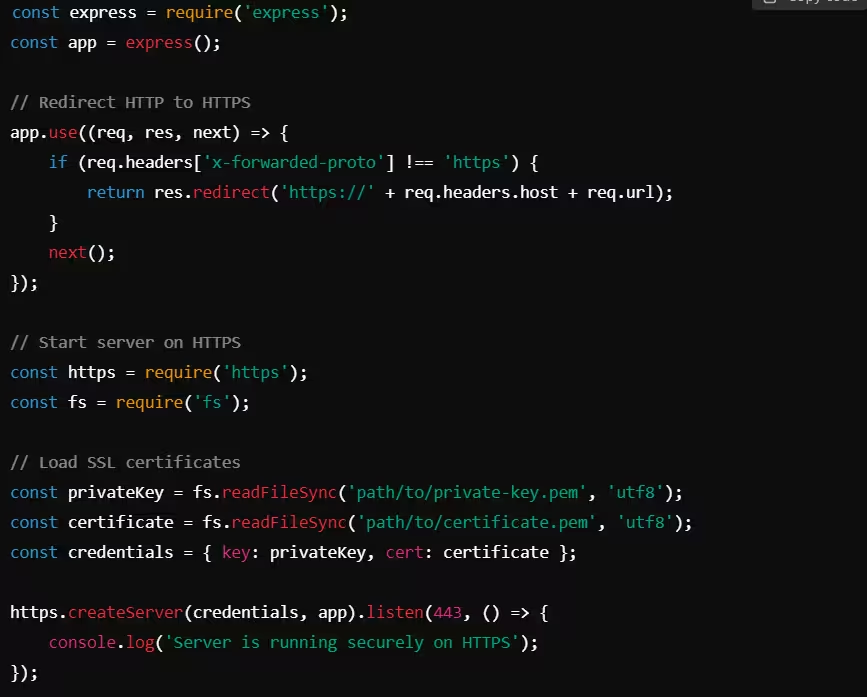
This Node.js example shows how to enforce HTTPS in an Express.js application by redirecting HTTP requests to HTTPS.
Setting Secure Cookies
Cookies are often used to store session IDs. To ensure that session cookies are not intercepted or manipulated by attackers, they must be configured with secure flags and attributes.
Secure cookie attributes:
- Secure flag: Ensures that cookies are only sent over HTTPS, preventing them from being transmitted in plain text.
- HttpOnly flag: Prevents client-side scripts (like JavaScript) from accessing the cookie, mitigating XSS attacks.
- SameSite attribute: Mitigates CSRF attacks by restricting the conditions under which cookies are sent. Use
SameSite=LaxorSameSite=Strictto prevent cross-site requests from sending cookies.
Example: Setting Secure Cookies in PHP
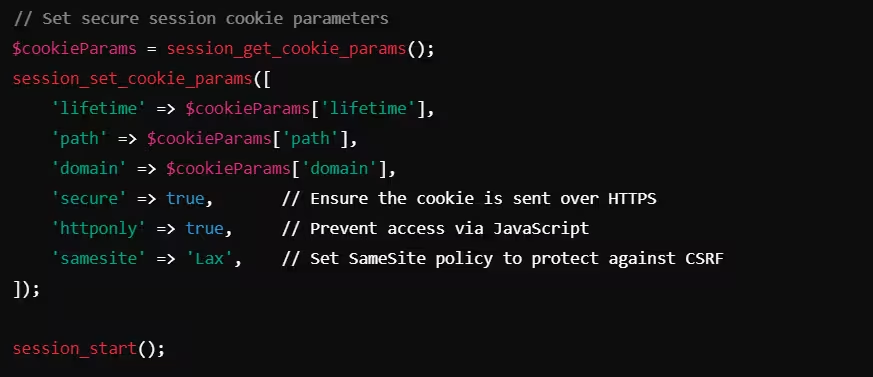
In this PHP example, session cookies are set with the secure, HttpOnly, and SameSite attributes, ensuring that they are sent securely and protected against XSS and CSRF attacks.
Implementing Proper Session Timeout Policies
To reduce the risk of unauthorized access, sessions should have a timeout policy. After a certain period of inactivity, the session should expire, forcing the user to re-authenticate. This limits the damage if a session is hijacked or left open on an unattended device.
Best practices for session timeouts:
- Set a short timeout for idle sessions (e.g., 15–30 minutes of inactivity).
- Optionally, implement absolute timeouts, where the session expires after a fixed period (e.g., 8 hours), regardless of user activity.
- Implement session warning notifications that alert users before their session expires, giving them the chance to extend their session.
Example: Implementing Session Timeout in Express.js (Node.js)
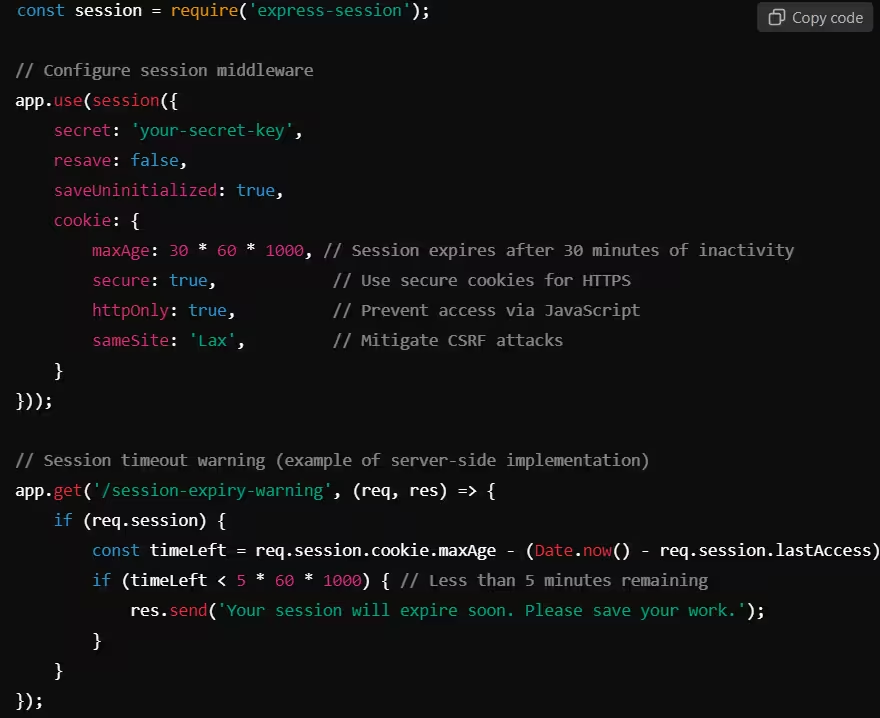
This Node.js example shows how to implement a session timeout of 30 minutes and send a warning when the session is about to expire.
Session Hijacking and Session Fixation Prevention
To protect against session hijacking, where attackers steal valid session IDs, and session fixation, where attackers force users to adopt a known session ID, certain measures should be taken:
- Regenerate session IDs: Always regenerate the session ID upon login, privilege escalation, and other sensitive actions.
- Limit session lifetime: By setting appropriate session timeouts and limits, the risk of session hijacking is reduced.
- Use secure session storage: Store session data in a secure, server-side location (e.g., databases or in-memory stores like Redis), and avoid storing sensitive data on the client side.
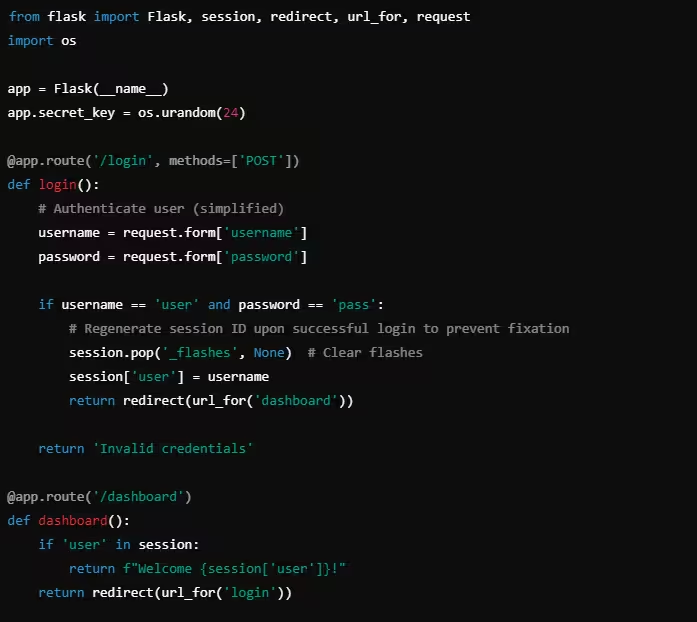
Example: Preventing Session Fixation in Python
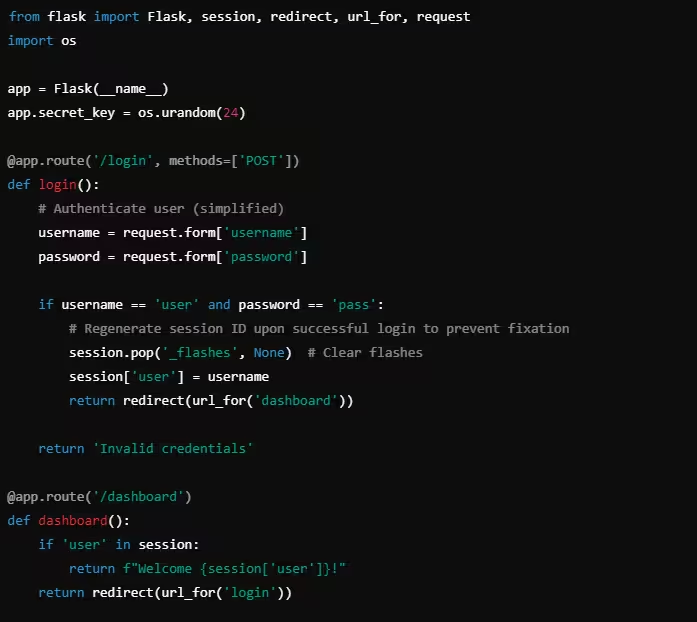
In this Flask example, the session ID is regenerated after the user successfully logs in, preventing session fixation attacks.
6. Session Termination and Logout
Proper session termination is another important aspect of secure session management. When users log out, their session should be properly destroyed, and the session ID should be invalidated.
Best practices for session termination:
- Destroy all session data upon logout.
- Invalidate session tokens server-side, preventing them from being reused.
Example: Secure Logout in PHP
In this PHP example, the session is securely destroyed, and the session cookie is deleted, ensuring that the session cannot be reused after logout.
Secure session management is essential for protecting user sessions from hijacking, fixation, and other forms of attack. By generating unique session IDs, using HTTPS for all session transmissions, setting secure cookie attributes, and implementing proper session timeout policies, you can significantly enhance the security of your web applications. Additionally, regularly regenerating session IDs, properly terminating sessions, and securing session storage will further protect your users and their data from common session-based vulnerabilities.
Learn more about WNE Security products and services that can help keep you cyber safe.
Learn about How to Create Secure Session Management: Best Practices for Web Applications and other new best practices and newly exploited vulnerabilities by subscribing to our newsletter.
Subscribe to WNE Security’s newsletter for the latest cybersecurity best practices, 0-days, and breaking news. Or learn more about “How to Create Secure Session Management: Best Practices for Web Applications” by clicking the links below



