WNE Security News
Read more about “How to Secure Secret Management: Avoid Embedding API Keys in Code” and the most important cybersecurity news to stay up to date with
How to Secure Secret Management: Avoid Embedding API Keys in Code

WNE Security Publisher
10/10/2024

Learn about How to Secure Secret Management: Avoid Embedding API Keys in Code and other new best practices and newly exploited vulnerabilities by subscribing to our newsletter.
Guide to Securely Managing Secrets: Avoid Embedding API Keys, Passwords, and Cryptographic Keys in Code
Embedding secrets like API keys, passwords, or cryptographic keys directly in source code is a serious security risk. Hardcoding secrets exposes your application to potential compromise, as source code can be shared, leaked, or accessed by unauthorized individuals. Attackers often look for secrets in code repositories, leading to breaches and unauthorized access to sensitive resources.
The best practice is to store secrets in secure places, such as environment variables or dedicated secret management services like AWS Secrets Manager or HashiCorp Vault. This guide explains why hardcoding secrets is dangerous, outlines alternative secure methods for storing and accessing secrets, and provides code examples for implementing these methods.
The Risks of Embedding Secrets in Source Code
Hardcoding secrets directly in the source code introduces several risks:
- Source code leaks: Code can be unintentionally leaked through version control systems (e.g., GitHub), collaboration tools, or shared repositories. If secrets are embedded in the code, they become easy targets for attackers.
- Limited flexibility: Hardcoded secrets make it difficult to change or rotate credentials, which is necessary to maintain good security hygiene.
- Exposure to multiple environments: Hardcoding keys in the source code means they could be exposed in all environments (development, staging, production), even where they are not needed.
To mitigate these risks, sensitive information should never be stored in code. Instead, use environment variables or secure secret management services.
Using Environment Variables to Store Secrets
One common and simple method for securely managing secrets is to store them in environment variables. This keeps secrets out of your source code while still allowing your application to access them as needed.
Advantages of environment variables:
- They are stored outside the codebase, reducing the risk of exposure.
- They can be easily configured for different environments (e.g., development, staging, production).
- Secrets are not visible in version control.
Example: Using Environment Variables in Node.js
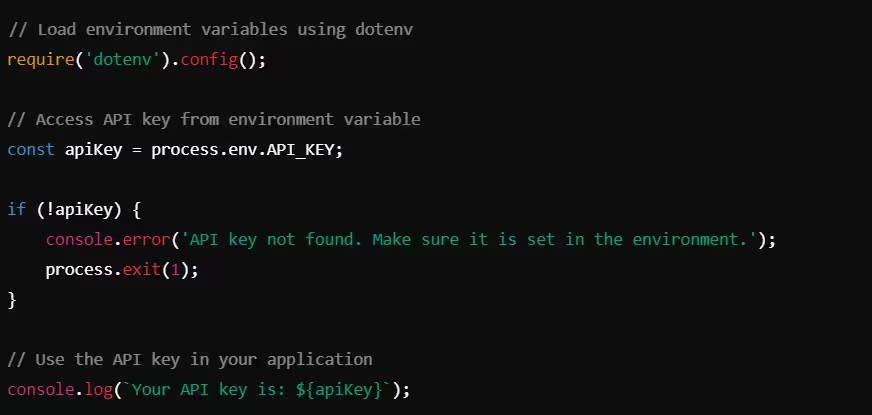
In this example, the API key is stored in an environment variable, making it easily configurable and preventing exposure in the source code. You can load environment variables from a .env file during development, which is not included in version control.
Example .env file:
Using Secure Secret Management Services
For larger applications or production environments, it’s better to use dedicated secret management tools like AWS Secrets Manager or HashiCorp Vault. These tools provide secure storage for sensitive data and offer features like automated secret rotation, access control, and auditing.
3.1. Using AWS Secrets Manager
AWS Secrets Manager allows you to securely store, manage, and retrieve secrets like API keys, database credentials, or cryptographic keys. It also integrates well with AWS services, making it easy to access secrets within your AWS-hosted applications.
Key features of AWS Secrets Manager:
- Automatic secret rotation: You can configure automatic secret rotation to meet compliance requirements and reduce the risk of stale secrets.
- IAM-based access control: Access to secrets can be managed via AWS IAM policies, ensuring that only authorized users or services can retrieve secrets.
- Audit logs: AWS CloudTrail logs secret access and changes, enabling visibility into secret usage.
Example: Retrieving Secrets from AWS Secrets Manager (Python)
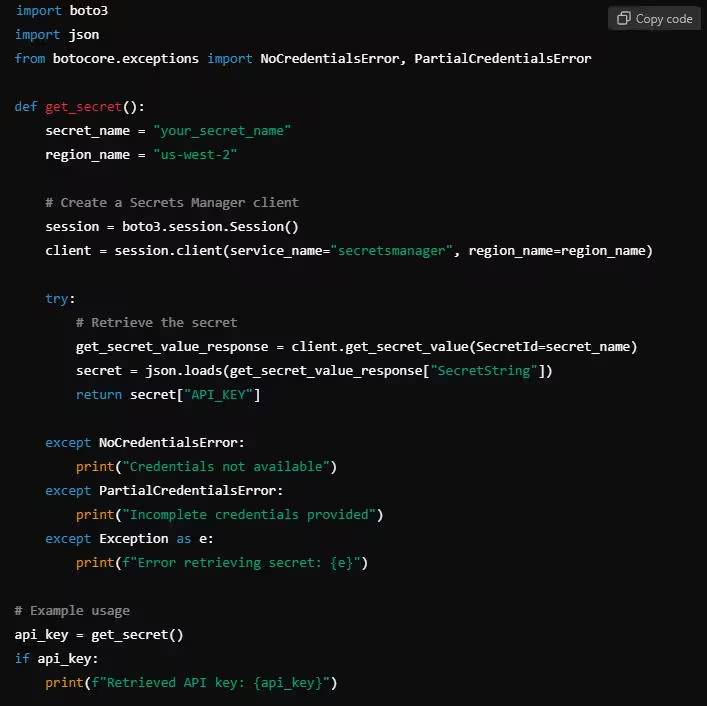
3.2. Using HashiCorp Vault
HashiCorp Vault is a robust tool for managing secrets, encryption keys, and access control policies. Vault is designed for both cloud and on-premises environments and can be integrated into any application stack.
Key features of HashiCorp Vault:
- Dynamic secrets: Vault can generate secrets on the fly, providing temporary, short-lived credentials to minimize exposure.
- Policy-based access control: Fine-grained policies define who or what can access specific secrets.
- Secret revocation and audit: Vault allows you to revoke secrets and provides detailed audit logs of access.
Example: Retrieving Secrets from HashiCorp Vault (Node.js)
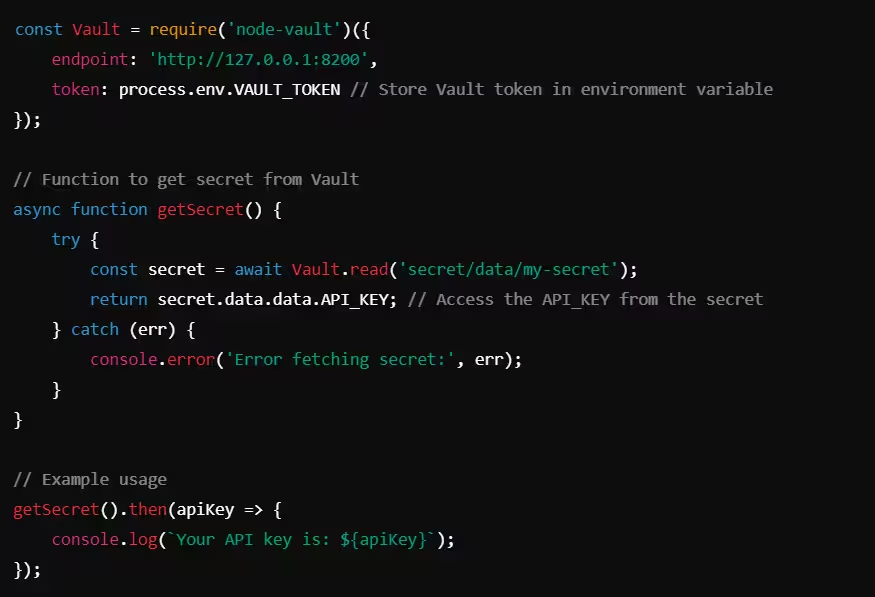
In this Node.js example, Vault securely stores and retrieves the API key. The Vault token is stored in an environment variable, further separating sensitive information from the codebase.
Securely Managing Access to Secrets
Managing access to secrets is just as important as storing them securely. Whether using environment variables or a secret management service, access control should be strictly enforced.
Best practices for managing access to secrets:
- Principle of least privilege: Only grant access to secrets to users or services that absolutely need them. Use role-based access control (RBAC) to limit access.
- Regularly rotate secrets: Rotate API keys, passwords, and other secrets periodically to reduce the risk of compromise.
- Monitor and audit secret access: Use logging and monitoring tools (e.g., AWS CloudTrail or Vault’s audit logs) to track when and how secrets are accessed. Investigate any suspicious access attempts.
Example: Securely Accessing Secrets in a Production Environment
For a production application running in a cloud environment (e.g., AWS), the following workflow can be implemented:
- Store secrets in AWS Secrets Manager.
- Use IAM roles to allow the application (e.g., an EC2 instance or Lambda function) to securely access Secrets Manager.
- Retrieve secrets at runtime: Secrets are retrieved as needed during runtime, ensuring they are never hardcoded in the application or exposed in logs.
Example: Accessing Secrets in AWS Lambda (Python)
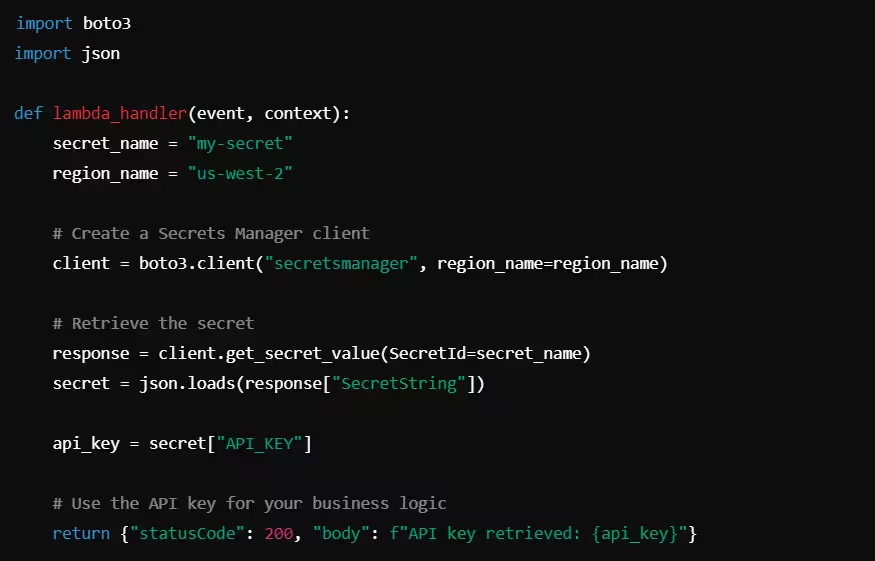
In this example, AWS Lambda securely retrieves the API key from Secrets Manager at runtime. The function uses IAM roles to access Secrets Manager, avoiding the need to store the API key in the function’s environment or code.
Avoid embedding secrets such as API keys, passwords, or cryptographic keys directly into source code. Doing so introduces significant security risks and makes your application more vulnerable to attacks. Instead, use environment variables for simple applications or secret management tools like AWS Secrets Manager or HashiCorp Vault for more complex environments. By securely managing secrets outside of the codebase, you ensure that sensitive information remains protected, access is controlled, and you can rotate secrets easily when necessary.
Learn more about WNE Security products and services that can help keep you cyber safe.
Learn about How to Secure Secret Management: Avoid Embedding API Keys in Code and other new best practices and newly exploited vulnerabilities by subscribing to our newsletter.
Subscribe to WNE Security’s newsletter for the latest cybersecurity best practices, 0-days, and breaking news. Or learn more about “How to Secure Secret Management: Avoid Embedding API Keys in Code” by clicking the links below



