WNE Security News
Read more about “How to Secure File Uploads: Validation, Sanitization, and Malware Scanning” and the most important cybersecurity news to stay up to date with
How to Secure File Uploads: Validation, Sanitization, and Malware Scanning

WNE Security Publisher
10/10/2024

Learn about How to Secure File Uploads: Validation, Sanitization, and Malware Scanning and other new best practices and newly exploited vulnerabilities by subscribing to our newsletter.
Guide to Validating and Sanitizing File Uploads
File uploads are a common feature in web applications, but they also pose a significant security risk if not properly handled. Malicious users can upload dangerous files, such as scripts, malware, or oversized files, that can lead to security breaches, data corruption, or resource exhaustion. To mitigate these risks, it is essential to validate and sanitize all file uploads, ensuring that only allowed file types and sizes are accepted, and to store files securely while scanning them for malware.
This guide outlines best practices for securely handling file uploads, including file type and size validation, secure file storage, and malware scanning. Specific code examples are provided to illustrate how to implement these practices in common programming languages.
1. Validating File Types
One of the most important steps in handling file uploads is validating the file type. Attackers can attempt to upload executable scripts or other dangerous files that can be executed by the server. To prevent this, applications should only accept specific, known-safe file types, such as images, PDFs, or text files.
Best practices for file type validation:
- Use a whitelist of allowed file types: Only allow specific file formats that are required for the application (e.g.,
.jpg,.png,.pdf, etc.). - Verify the file’s MIME type: Do not rely solely on the file extension, as it can be spoofed. Instead, check the MIME type to verify the actual file content.
Example: File Type Validation in Node.js
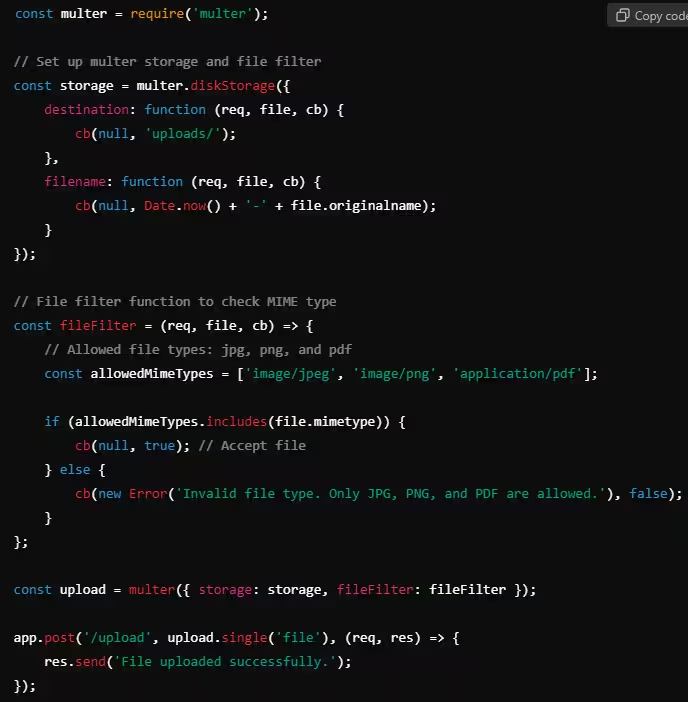
In this example, the fileFilter function ensures that only .jpg, .png, and .pdf files are accepted, based on their MIME types. This prevents potentially dangerous file types from being uploaded.
2. Validating File Size
Another important aspect of file upload security is limiting the file size. Accepting overly large files can lead to denial-of-service (DoS) attacks or resource exhaustion, which can overwhelm your application and cause performance issues.
Best practices for file size validation:
- Set maximum file size limits for uploads based on your application’s requirements.
- Reject files that exceed the allowed size before saving them to disk.
Example: File Size Validation in Express.js
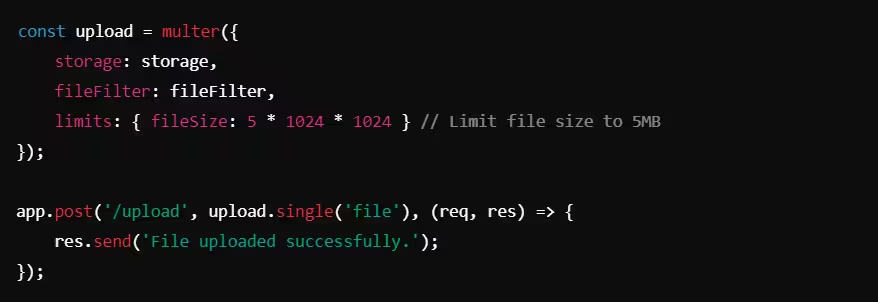
In this example, the limits option in Multer is used to restrict the maximum file size to 5MB. Files exceeding this size will be automatically rejected.
3. Sanitizing File Names
Uploaded files should not retain their original filenames, as they could contain special characters or malicious scripts. It’s important to sanitize or rename files to ensure safe storage.
Best practices for sanitizing file names:
- Remove or escape special characters that could be interpreted as part of a command.
- Rename files using unique identifiers, such as timestamps or UUIDs, to avoid conflicts and prevent malicious behavior.
Example: File Name Sanitization in Python (Flask)
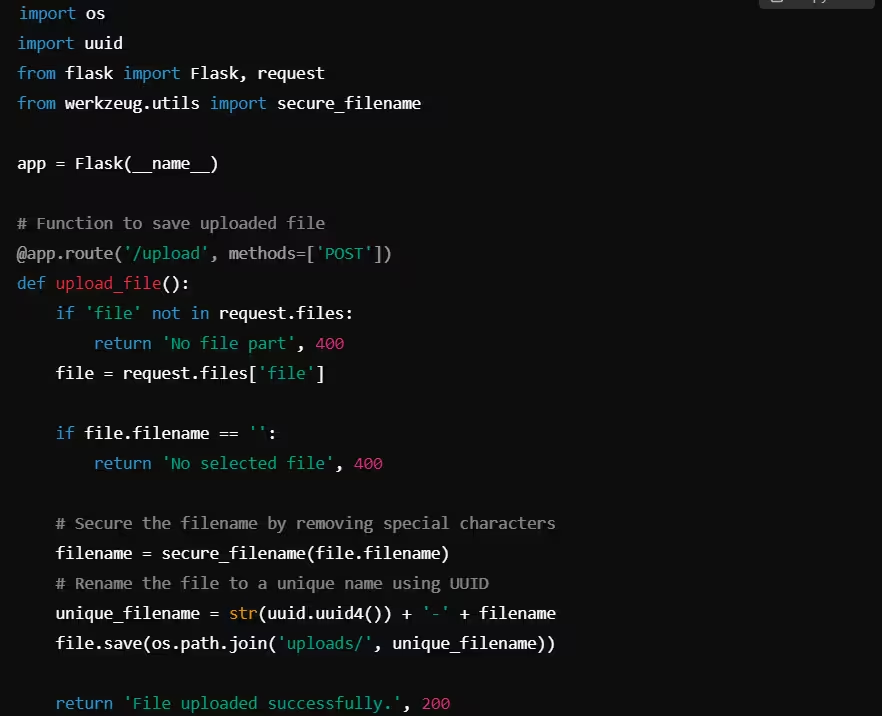
In this example, the secure_filename() function from Flask ensures that special characters in filenames are removed, and the filename is renamed using a UUID to ensure uniqueness.
4. Storing Files Securely
Once validated and sanitized, files should be stored in a secure location. It is critical that uploaded files are not stored in publicly accessible directories, as this could allow attackers to directly access and execute malicious files.
Best practices for secure file storage:
- Store files outside the web root: Ensure that uploaded files are not directly accessible from the web server.
- Apply strict access controls to the directory where files are stored. Only authorized users or processes should be able to access the files.
Example: Secure File Storage in PHP
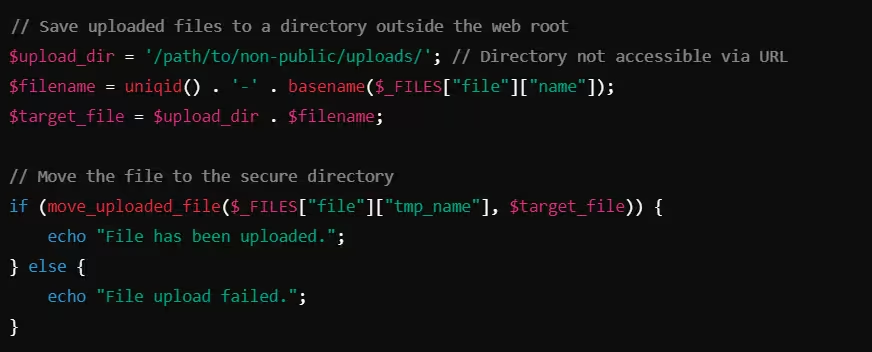
In this example, uploaded files are saved in a directory outside the web root, ensuring that they cannot be accessed directly via URL.
5. Scanning Uploaded Files for Malware
Even after validating the file type and size, it’s important to scan uploaded files for malware to ensure they do not contain malicious code or executables.
Best practices for malware scanning:
- Use a malware scanning tool such as ClamAV or integrate with an antivirus API to scan files as soon as they are uploaded.
- Set up automated alerts or quarantines for suspicious files.
Example: Using ClamAV to Scan Files (Node.js)
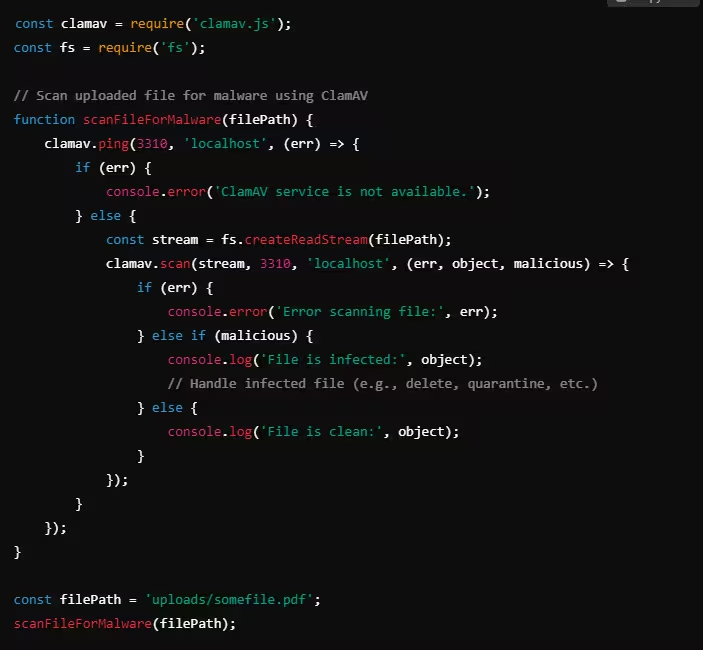
In this example, ClamAV is used to scan uploaded files for malware. If a file is found to be malicious, appropriate actions, such as deleting or quarantining the file, can be taken.
6. Monitoring and Logging File Uploads
Monitoring and logging file uploads is important for security and auditing purposes. All upload activities should be logged, including the time of the upload, the user who uploaded the file, the file name, and any validation or malware scanning results.
Best practices for logging file uploads:
- Log all file upload events, including successful and failed uploads.
- Record metadata such as the file name, size, user ID, and validation status.
- Regularly review logs for suspicious activity, such as unusual file types or repeated failed upload attempts.
Example: Logging File Uploads in Python (Flask)
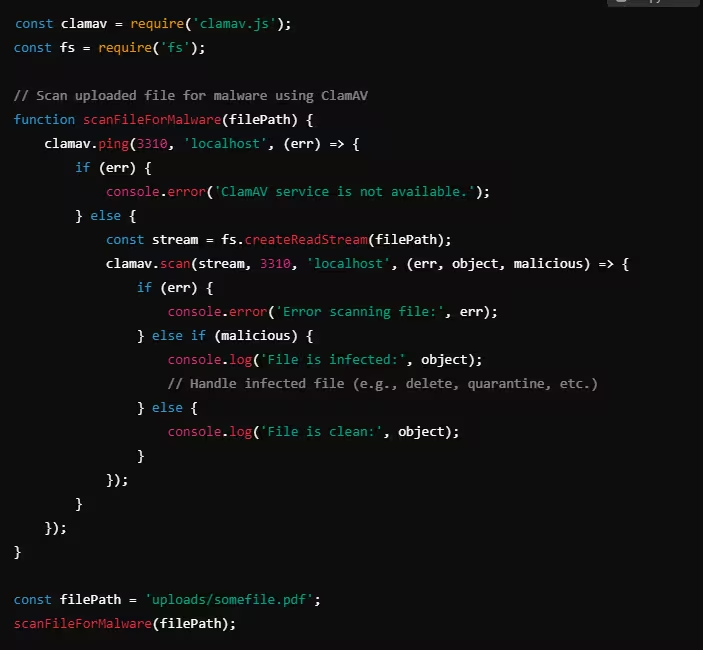
In this example, the file upload activity is logged, including the file name, size, and the IP address of the user who uploaded the file. Logs can later be.
Learn more about WNE Security products and services that can help keep you cyber safe.
Learn about How to Secure File Uploads: Validation, Sanitization, and Malware Scanning and other new best practices and newly exploited vulnerabilities by subscribing to our newsletter.
Subscribe to WNE Security’s newsletter for the latest cybersecurity best practices, 0-days, and breaking news. Or learn more about “How to Secure File Uploads: Validation, Sanitization, and Malware Scanning” by clicking the links below



