WNE Security News
Read more about “How to Secure Error Handling and Logging Best Practices for Web Apps” and the most important cybersecurity news to stay up to date with
How to Secure Error Handling and Logging Best Practices for Web Apps

WNE Security Publisher
10/10/2024

Learn about How to Secure Error Handling and Logging Best Practices for Web Apps and other new best practices and newly exploited vulnerabilities by subscribing to our newsletter.
Guide to Implementing Proper Error Handling and Secure Logging
Proper error handling is a critical component of secure software development. When errors occur, they can inadvertently expose sensitive information such as stack traces, database queries, internal system details, or even personal user data. This can provide attackers with valuable insight into your system’s inner workings, making it easier for them to exploit vulnerabilities. Similarly, improper logging practices can lead to the exposure of sensitive information, including passwords or personally identifiable information (PII), which should never be logged.
In this guide, we’ll explore the best practices for implementing secure error handling and logging, highlighting what to avoid and providing code examples to ensure you’re handling errors securely while protecting sensitive data.
The Importance of Proper Error Handling
When an application encounters an error, it’s important to manage the error gracefully. This prevents:
- Sensitive information leakage: Error messages should never reveal technical details such as database structures, internal server paths, or stack traces to users.
- Exploitation by attackers: Revealing too much information in an error message can provide attackers with clues on how to breach the system.
Best Practices for Error Handling:
- Provide generic error messages to end-users that do not expose system details.
- Log detailed errors on the server side for debugging and auditing, but never expose these logs to users.
- Differentiate between user-facing messages and developer-facing logs. The user should only receive a simple message like “An error occurred, please try again later,” while detailed information (if needed) should be logged internally.
Avoid Exposing Sensitive Information in Error Messages
Sensitive information that should never be exposed in error messages includes:
- Stack traces
- Database queries or connection strings
- Internal API keys or credentials
- Server file paths or environment variables
Example of Bad Error Handling (PHP)
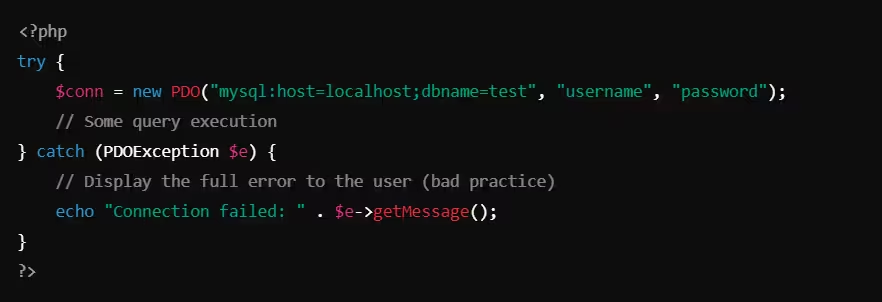
What’s wrong?
- This code directly exposes the error message to the user, revealing sensitive information about the database structure and server.
Example of Proper Error Handling (PHP)
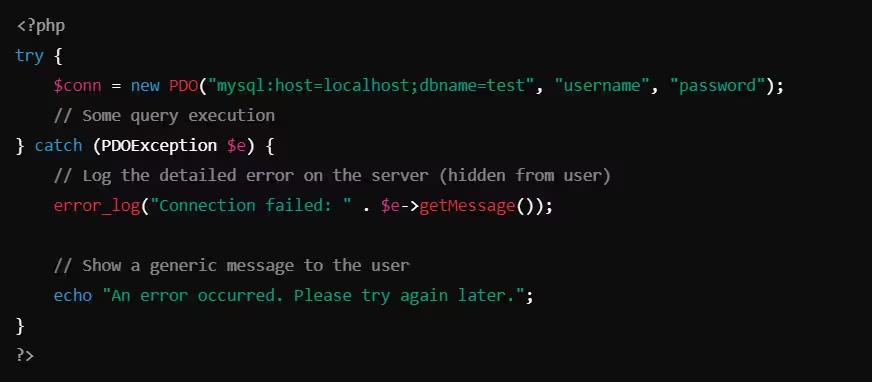
What’s improved?
- The detailed error is logged using
error_log(), but the user only sees a generic error message that does not reveal system details.
Log Events Securely
Logging events is important for troubleshooting, monitoring, and auditing, but logs must be managed securely to prevent sensitive data exposure. The primary risks associated with improper logging include logging sensitive information such as passwords, API keys, credit card numbers, or personal data (e.g., names, addresses, or social security numbers).
Best Practices for Secure Logging:
- Avoid logging sensitive data: Never log passwords, tokens, personal data (PII), or financial information.
- Anonymize or mask sensitive data when logging. For example, only log part of an email address (e.g.,
joh***@example.com) or partially mask credit card numbers. - Use secure storage for logs: Ensure that logs are stored securely with proper access controls in place to prevent unauthorized access.
- Implement log rotation: Logs should not grow indefinitely. Use log rotation to manage log file sizes and retention periods securely.
Example: Secure Logging in Python (Avoiding Sensitive Data)
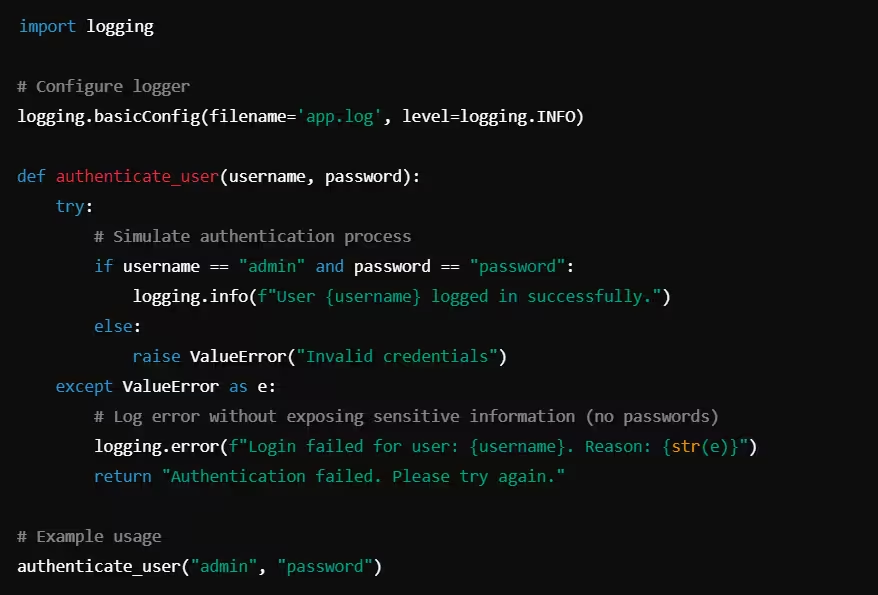
What’s correct?
- The username is logged, but the password is not included in the log file.
- If an error occurs, a generic message is logged and returned to the user without exposing sensitive data.
Masking and Anonymizing Data in Logs
When logging sensitive information is unavoidable, such as logging failed login attempts or user activities, it is important to anonymize or mask the data to minimize exposure.
Example: Masking Sensitive Data (JavaScript)
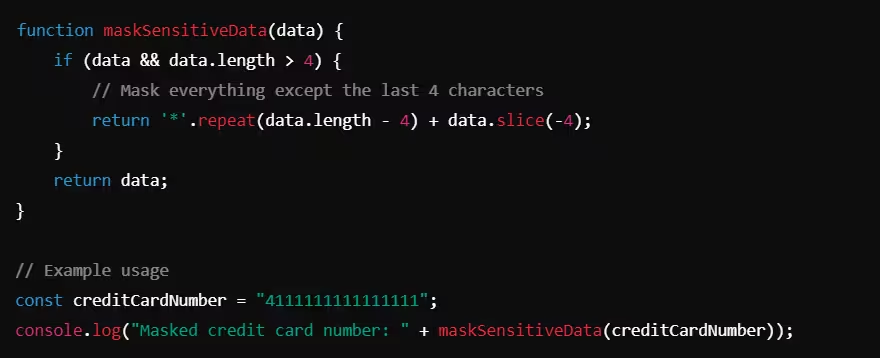
Output:
Masked credit card number: ************1111
What’s correct?
- Only the last four digits of the credit card number are shown in the logs, reducing the risk of data leakage if logs are accessed.
Centralized Logging and Monitoring
Implement centralized logging to ensure that logs are consistently monitored and stored securely. Centralized logging systems like ELK Stack (Elasticsearch, Logstash, Kibana), Splunk, or Graylog can aggregate logs from multiple systems into a single location, making it easier to monitor and analyze logs for potential security incidents.
Benefits of centralized logging:
- Centralized access control and encryption for logs.
- Simplified log monitoring for suspicious activity.
- Easier log correlation across multiple services for auditing and compliance.
Example: Using Winston for Centralized Logging (Node.js)
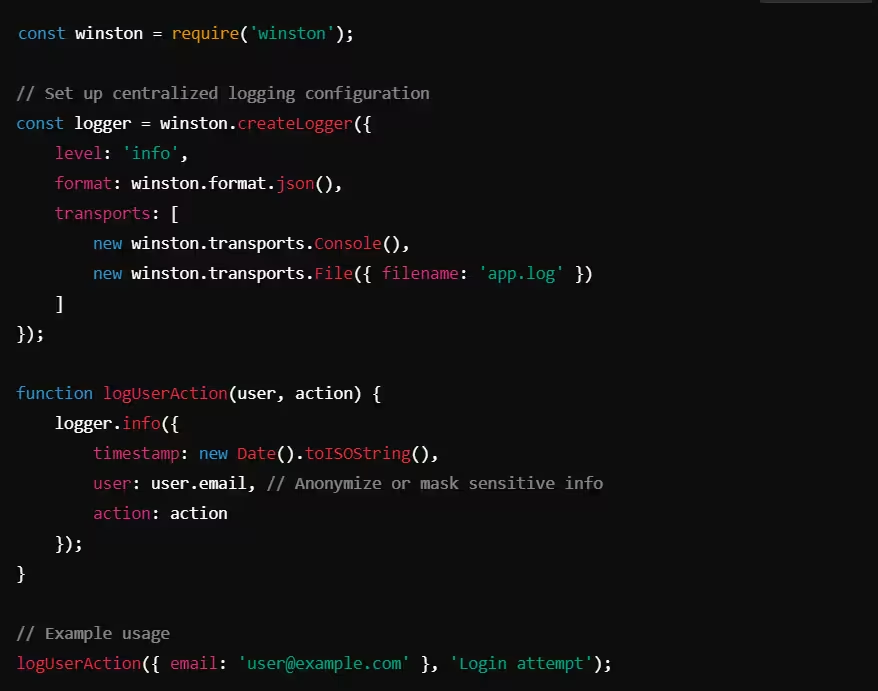
In this Node.js example, Winston is used to log events securely, ensuring that sensitive information like user email addresses can be masked or anonymized in the logs.
Error and Exception Reporting in Production
In production environments, never expose detailed error messages to users. Instead:
- Use custom error pages to handle unexpected errors gracefully, providing users with a simple, non-technical message.
- Log the full error details on the server side for investigation.
Example: Custom Error Pages (Express.js)
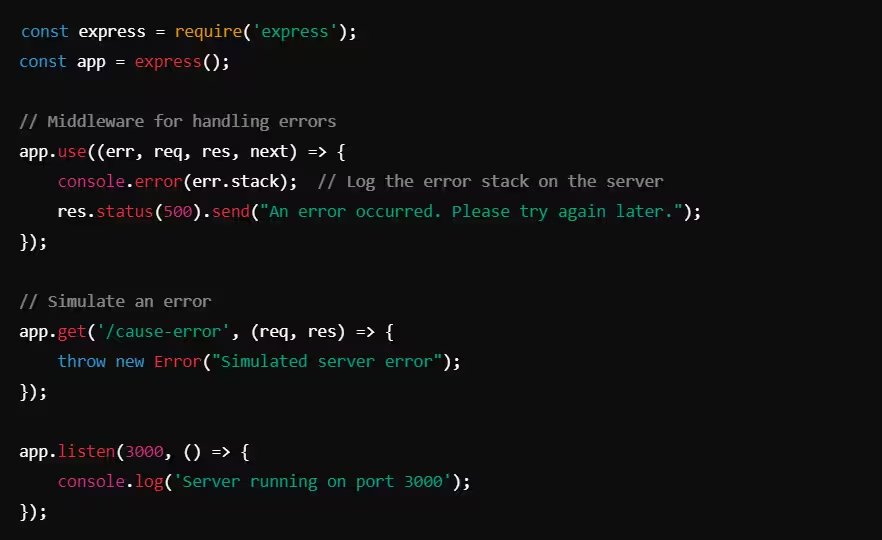
What’s correct?
- The error details are logged on the server for debugging purposes, but the user receives a generic message without revealing internal system details.
Proper error handling and secure logging are essential to protecting sensitive data and ensuring the security of your web applications. By providing generic error messages to users, securely logging events without sensitive information, and ensuring logs are centralized and monitored, you can mitigate the risks associated with improper error handling. Following these best practices ensures that your system remains robust and secure while providing clear and actionable logging for developers and administrators.
Learn more about WNE Security products and services that can help keep you cyber safe.
Learn about How to Secure Error Handling and Logging Best Practices for Web Apps and other new best practices and newly exploited vulnerabilities by subscribing to our newsletter.
Subscribe to WNE Security’s newsletter for the latest cybersecurity best practices, 0-days, and breaking news. Or learn more about “How to Secure Error Handling and Logging Best Practices for Web Apps” by clicking the links below



